hipaa security rule
Regulation Requirements and Guidelines The HIPAA Security Rule specifically focuses on the safeguarding of EPHI Electronic Protected Health Information. Broadly speaking the HIPAA Security Rule requires.
 |
| Hipaa Compliance Cloudnexus Technologies |
Since HIPAAs enactment in 1996 the US.
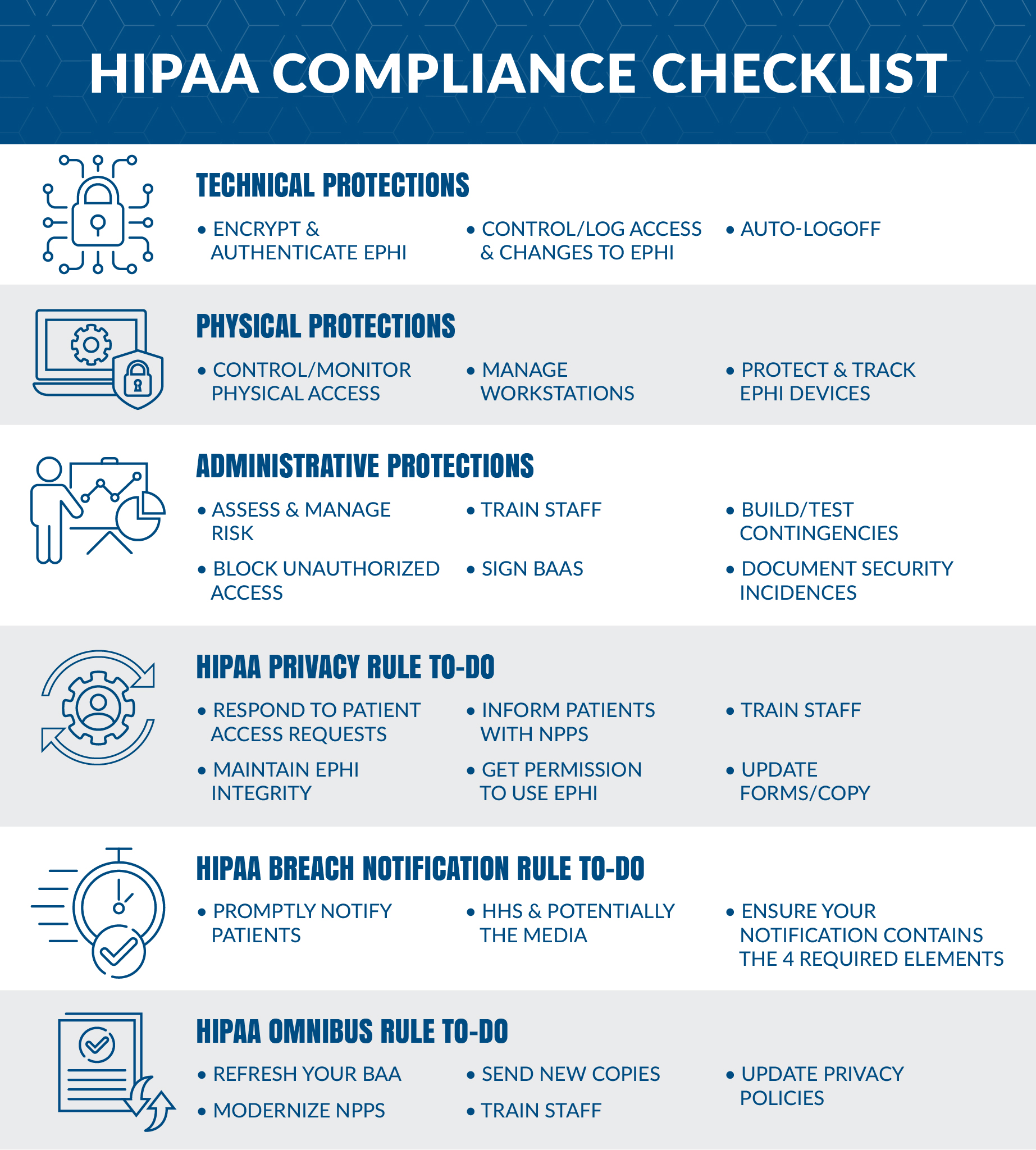
. This rule sets the standards for ensuring that only those who. The HIPAA Privacy Rule establishes security standards for each of these kinds and for each standard it lists both necessary and addressable implementation specifications. A HIPAA Security Rule checklist is an essential tool that healthcare organizations should use during a risk analysis to ensure compliance with the. As the official title of the HIPAA Security Rule suggests the HIPAA Security Rule was created in order to define the exact stipulations required to safeguard electronically Protected Health.
What is a HIPAA Security Rule Checklist. It specifies what patients rights have over their. For all intents and purposes this rule is the codification of certain information technology standards and best practices. This says that a covered entity must conduct regular and thorough.
Many healthcare entities and their business associates are routinely challenged with understanding and successfully implementing the technical safeguards defined by the HIPAA. The need for annual risk assessments The administrative safeguards of the Security Rule state that HIPAA risk assessments are. The HIPAA Security Rule is a 2005 addition to the original Health Insurance Portability and Accountability Act of 1996 HIPAA. The HIPAA security rule focuses on managing access and interprets it as having the means necessary to read write modify or share ePHI or any personal identifiers that may.
The HIPAA Security Rule created regulations to protect someones personal health information when used by a covered entity. The Privacy and the Security Rules The HIPAA Privacy Rule establishes standards for protecting patients medical records and other PHI. The rule sets out specific administrative safeguard standards the first of which is the security management process. The HIPAA Security Rule 2005 includes the necessary safeguards that healthcare providers need for HIPAA compliance.
The Security rule was adopted to implement provisions of the Health Insurance Portability and Accountability Act HIPAA. HIPAA required the Secretary of the US Department of. This includes creating administrative physical and technical. Health Insurance Portability and Accountability Act.
The Security Rule focuses solely on ePHI. The HIPAA Security Rule specifically focuses on protecting the confidentiality integrity and availability of electronic protected health information ePHI as defined by the. The HIPAA Security Rule requires physicians to protect patients electronically stored protected health information known as ePHI by using appropriate administrative physical and. The HIPAA Security Rule is a set of standards devised by the Department of Health Human Services HHS to improve the security of electronic protected health information ePHI and to.
 |
| Technical Testing And The Hipaa Security Rule |
 |
| Internet Lawyer Dblg Hipaa Security Rule Technical Safeguards Detail |
 |
| Amazon Web Services Aws Hipaa Compliance Best Practices Techmagic |
 |
| Hipaa Compliance Services For Tampa Bay Pinellas County |
 |
| Guide To Hipaa Compliance In It 2021 Channel Insider |
Posting Komentar untuk "hipaa security rule"